Enabling PowerShell 2.0 Remoting in an Enterprise
Remoting is one of the great new features in PowerShell 2.0. If you wish to deploy PowerShell 2.0 and remoting within your Enterprise you probably don’t want to run Enable-PSRemoting on every single server where you have installed PowerShell 2.0. The smart way is of course to use Group Policy. You will need to ensure the following:
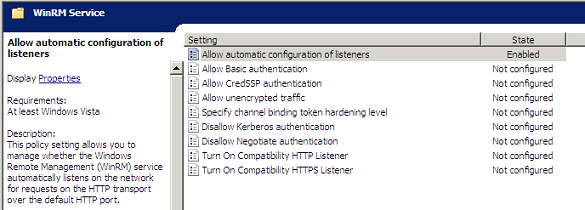
- Enable the policy Computer Configuration\Policies\Administrative Templates\Windows Components\Windows Remote Management\WinRM Service\Allow automatic configuration of listeners, specifying IPv4 and V6 subnets where appropriate:
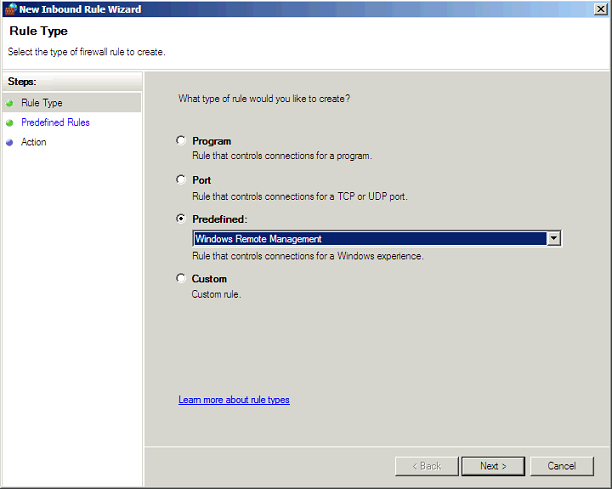
- If you have Windows Firewall enabled on your servers you will need to make a policy setting to allow inbound Windows Remote Management. Create a new Inbound rule within Computer Configuration\Policies\Windows Settings\Security Settings\Windows Firewall with Advanced Security\Inbound Rules
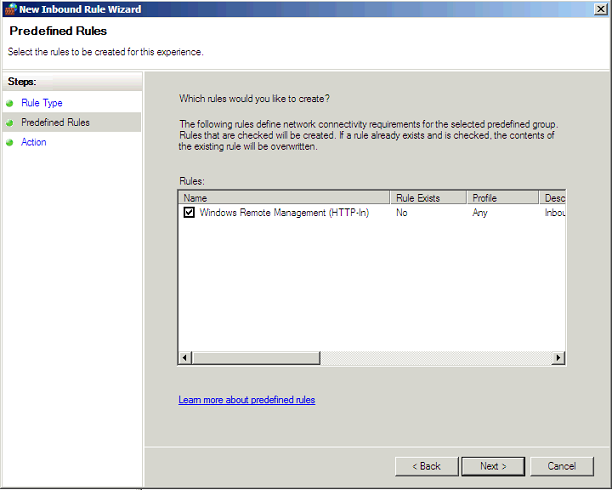
New Predefined Rule: Windows Remote Management:
Accept the rule:
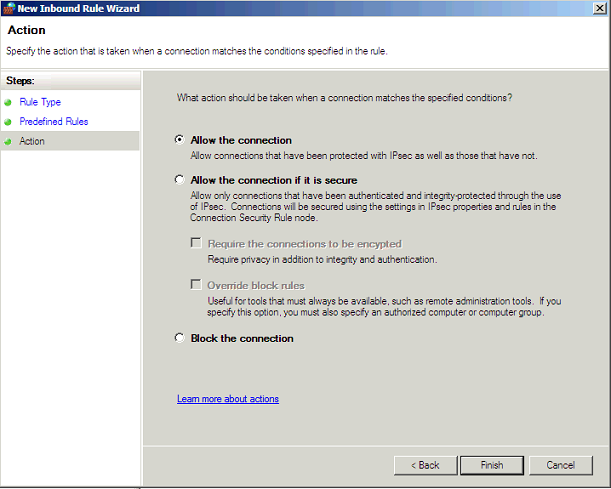
Select Allow and Finish:
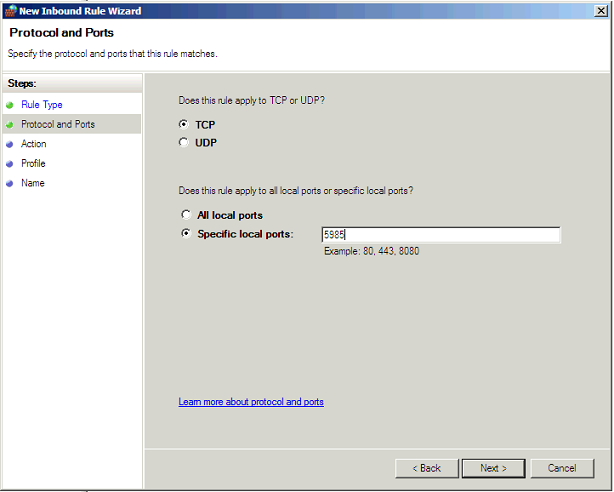
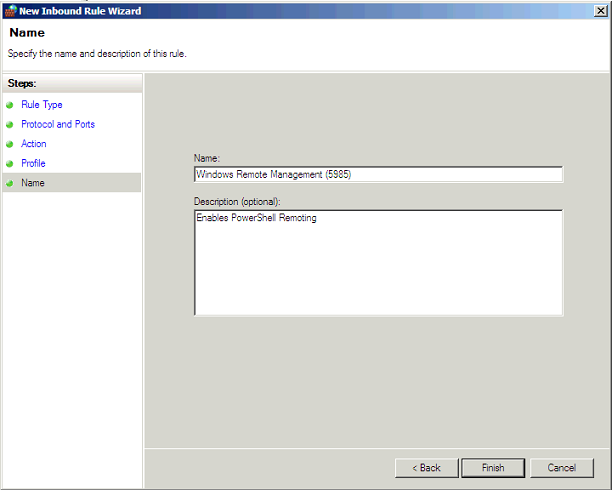
Note: If you perform the above on a server previous to 2008 R2 it will create the rule on port 80 not 5985 which is what you need for PowerShell remoting. So instead you will need to create a new custom rule using 5985 as the port number.
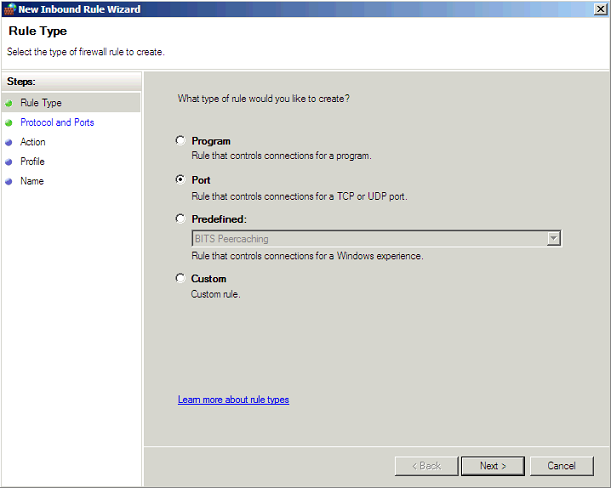
New Port rule:
Set the port to 5985:
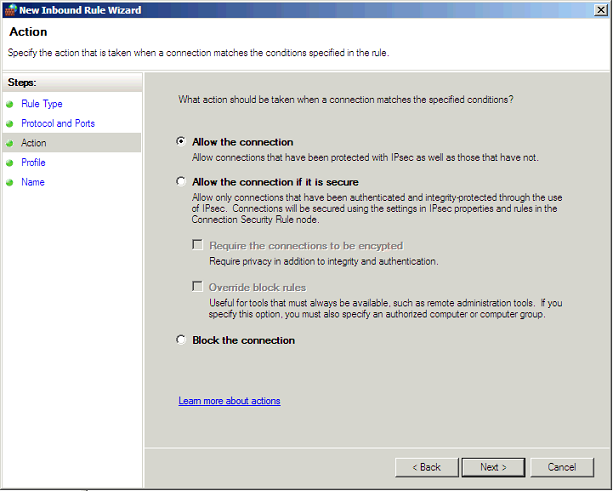
Select Allow:
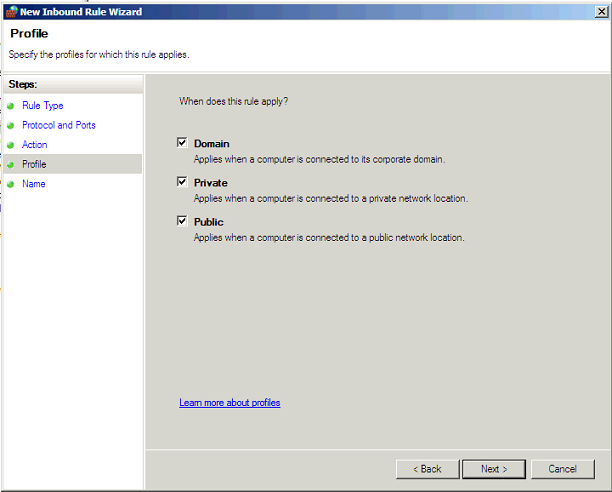
Choose which network profiles are required:
Give it a meaningful name:
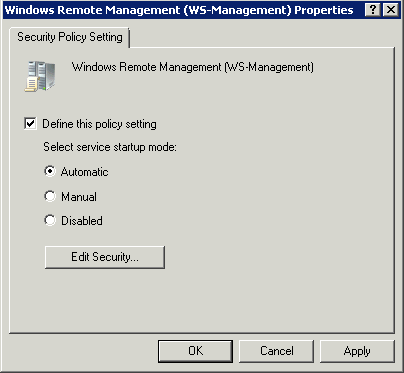
- Finally the WinRM service should be Started and set to Automatic. On server versions of Windows this is the default, on clients not. If you wish to ensure this is the case you could make a Group Policy setting using Computer Configuration\Policies\Windows Settings\Security Settings\System Services\Windows Remote Management and setting it to Automatic.
Remote away!